Update or Replace SAML Certificate In Azure for Workspace One Access
Update or Replace SAML Certificate In Azure for Workspace One Access
Update/Replace SAML Certificate
1. Generate a new certificate: Create a new SAML certificate to replace the expiring one. Ensure that the new certificate meets the necessary requirements, such as key length and algorithm compatibility.
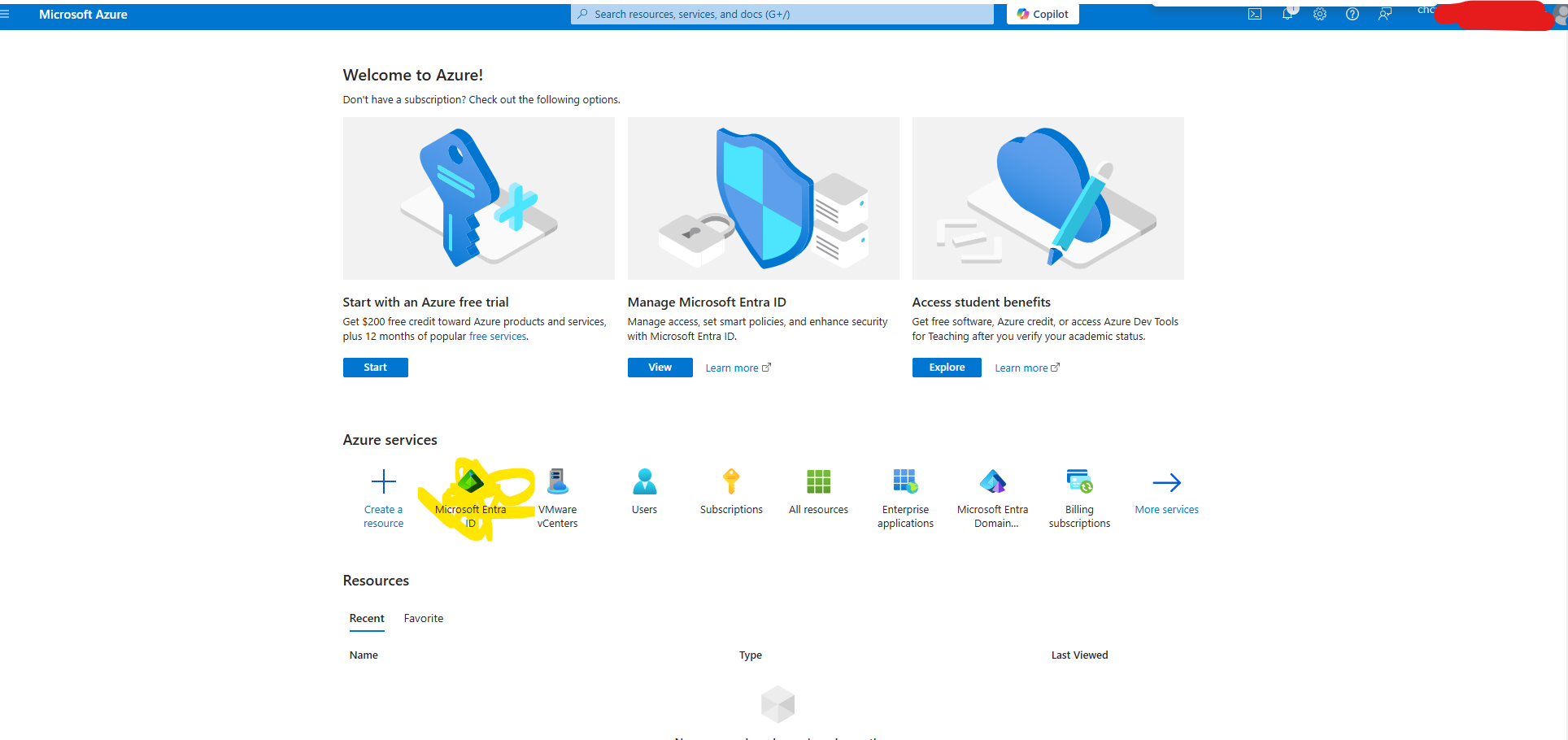
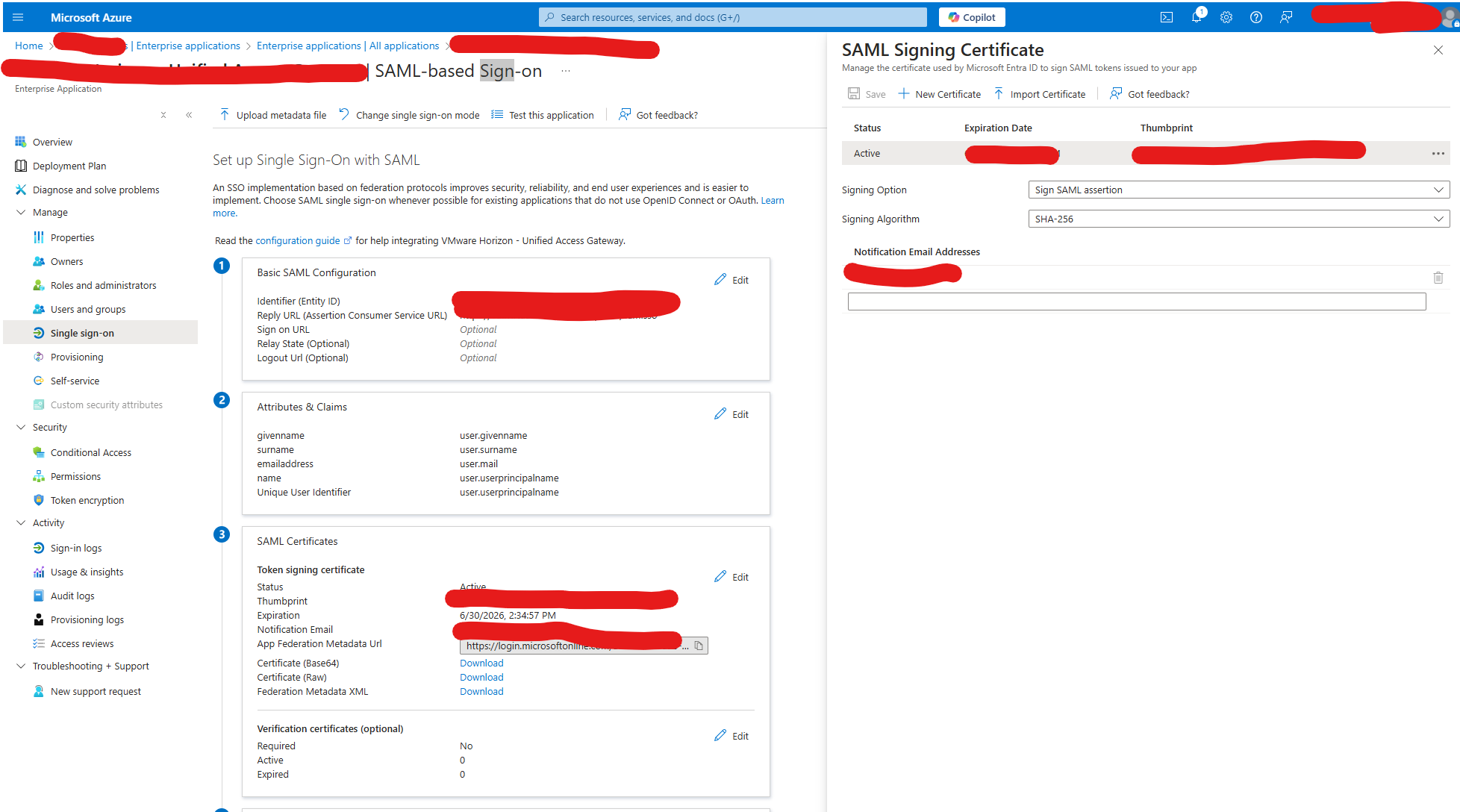
2. Update the certificate in Azure AD: Go to the Azure portal, navigate to the Azure Active Directory section, and locate the Enterprise Applications or App Registrations area where your Workspace ONE Access integration is configured. Update the SAML signing certificate with the new one. Simply generate a new certificate per the screenshot below. After you click edit on the SAML certificates it pops up a modal on the right. Click the + new certificate button. This will be your new certificate. it will be marked as inactive make sure to download this certificate and wheny ou are done mark it as active for testing.
Home>Entra ID Directory > Enterprise applications>All applications> (your ws1 application name)
3. Update the certificate in Workspace ONE Access: Access the Workspace ONE Access console and update the SAML configuration with the new certificate. This typically involves uploading the new certificate to the identity provider settings within Workspace ONE Access.
Important: Before you process metadata make sure to take a screenshot of the configuration. I’ve noticed when you process the metadata it losses the values. For example: “name ID format mapping from SAML response” section could become missing. We’ll want ot make sure we can re-configure those appropriatly if they become erased.
Workspace one Access Admin console> Integrations > Identity providers > (Your Configuration) process metadata and save
Only if the session expires will they need to authenticate.
What’s New In Horizon 2309 – Now Generally Available
What’s New In Horizon 2309 – Now Generally Available
Overview
Just released and made generally available on 10/26/2023 is Horizon Version 2309. This is the most current release of Horizon View from VMware. As a reminder this is a majority of the updates below. Look to the links below in the release notes section for full feature information and any additional updates should they happen from VMware.
Horizon Server and Instant Clones
- Session load distribution across CPA pods (load Index approach)
- Published Apps on Demand option to accept App Volumes Manager certificate thumbprint when adding to Horizon.
- Allow Edge Gateway to consume events from Horizon Connection Servers.
- Forensics – enable protection of held VMs from accidental deletion.
- Leverage sysprep workflow to create computer accounts and perform domain join.
- OpenSSL 3.0 upgrade for Connection Server
Client and Agent Release
- RDSH application launch limit
- Per-RX bandwidth reporting.
- Separate screen recording from screen capture blocking.
- Volume improvements.
- ARM Windows support for USB.
- OpenSSL 3.0 upgrade for all clients/agent/etc..
App Volumes
- vSphere 8: True Read-only Feature enablement per Center.
- AVM credential support for file shares.
- Published Apps on Demand option to accept AVM cert thumbprint in Horizon.
- App Volumes in AVD Remote Apps. About App Volumes Deployment on Azure
- App Volumes in Amazon AppStream 2.0. Workflow of App Volumes for Amazon AppStream 2.0
Dynamic Environment Manager
- Dynamic configuration of Horizon FIDO2 web authentication redirection for users.
- Dynamic configuration of Horizon storage drive redirection for users.
- Support for configuring non-policy locations in ADMX-based settings.
Unified Access Gateway
-
Certified support for deploying UAG on Azure in FIPS mode with Smart Card authentication with the Blast Secure Gateway.
-
Added disk usage statistics to the log archive for troubleshooting purposes.
-
Logging improvements.
-
Updates to Photon OS package versions and Java versions.
Release Notes
- Horizon Server
- Horizon Client for Android
- Horizon Client for Chrome
- Horizon Client for iOS
- Horizon Client for Linux
- Horizon Client for Mac
- Horizon Client for Windows
- Horizon HTML Access
- App Volumes
- Dynamic Environment Manager
Documentation
VMware Horizon Apps On Demand Launch Behavior How Does It Work?
VMware Horizon Apps On Demand Launch Behavior How Does It Work?
Overview
Have you ever been curious about the process that takes place when you initiate an on-demand launch of an App Volumes application on a Windows Server RDS host? Specifically, let’s consider a scenario where you or your user connects and launches a published app on demand.
Steps
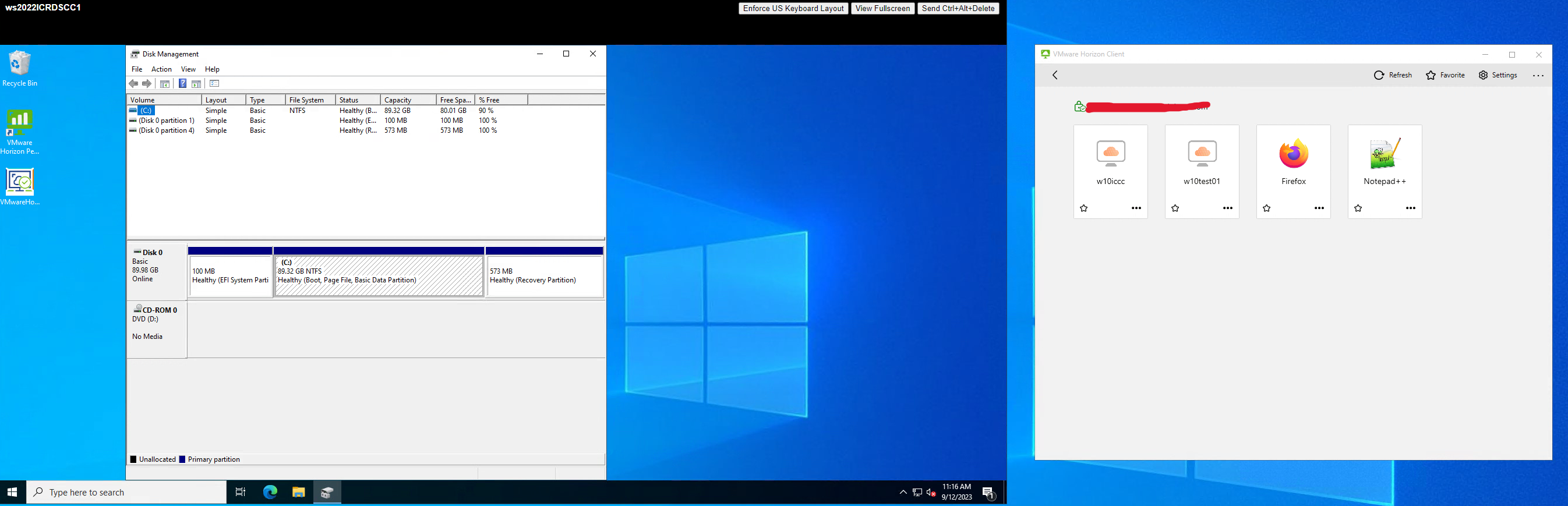
- User clicks the published app on demand.
2. The App Package is presented to the RDS host via a mounted drive from Horizon View and App Volumes.
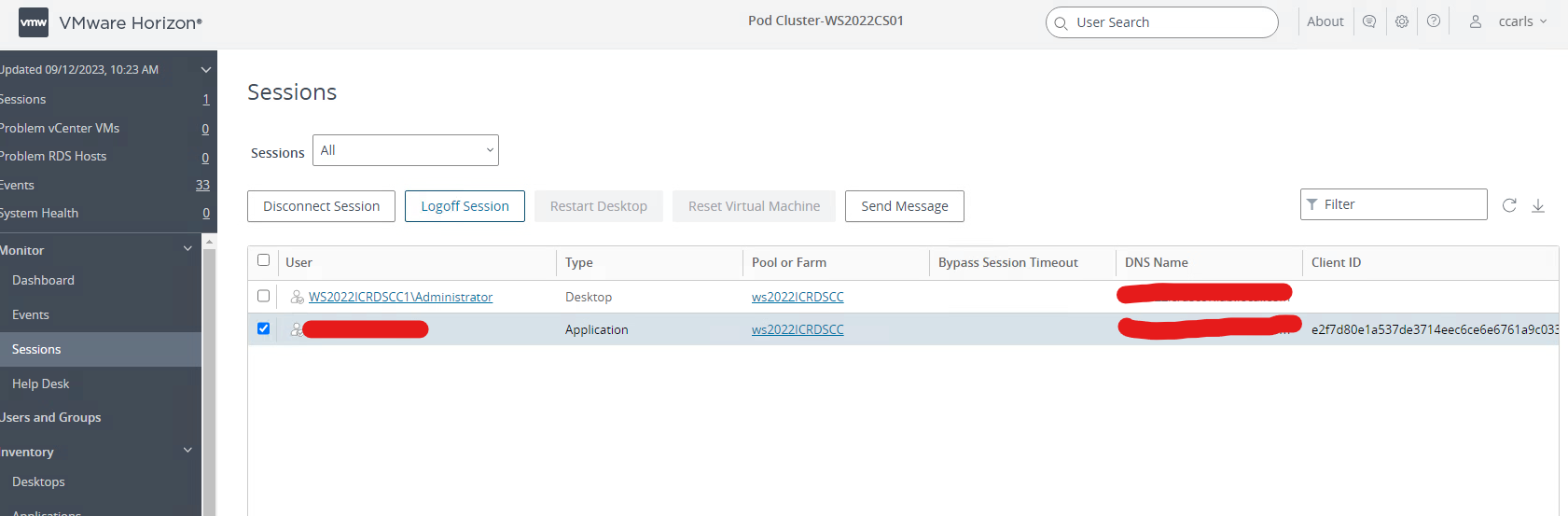
3. I am going to now logoff the user and see what happens. Keep in mind this is the only user logged into the machine so since that is the case no one else needs the app. It removes the applications that I was using.
4. As you can see the mounted drives are removed. This is a great feature that allows you to use the same images for multiple applications/use cases. Most times we create specialized farms to entertain certain uses causes which drives friction and complexity
VMware Horizon Client and Agent FIDO2 Redirection Feature
VMware Horizon Client and Agent FIDO2 Redirection Feature
Overview
Just released and made generally available on 07/06/2023 is Horizon Version 2306. This is the most current release of Horizon View from VMware. As a reminder this is a majority of the updates below. Look to the links below in the release notes section for full feature information and any additional updates should they happen from VMware.
This particular release has a ton of cool new enhancements around app volumes and our client agent release (CART). In particular for app volumes we have announced App Volumes Manager on Azure AVD with Azure File Shares (Solution Preview)and App Volumes for Amazon AppStream 2.0 Technical PreviewIn future posts I will be going over some these enhancements.
Horizon Server and Instant Clones
- Session load distribution across CPA pods (Session Count approach).
- Block connection to server if client doesn’t validate certificates.
- Allow admins to configure certificate mapping.
- Persistent disk support for Instant Clones.
- Provide fixed timer for discarding SSO credentials without disconnecting Desktops/Apps.
Client and Agent Release
- Horizon Recording support for LinuxVDI.
- Fido2 WebAuthN redirection Windows Client.
- DEEM: Mac client & .pkg installer
- Mac scanner forward vendor-specific options.
App Volumes
- AV Manager on Azure AVD with Azure File Shares (Solution Preview)
- vSphere 8: Package Attachment Resiliency
- Apps On Demand: URI launch
- App Volumes for Amazon AppStream 2.0 Technical Preview
Dynamic Environment Manager
- Support for periodically refreshing DEM configuration.
- Support for collecting telemetry data from DEM Management console
- Support for configuring Horizon. browser content redirection policy.
Unified Access Gateway
-
Added compatibility with Horizon Connection Server’s support for setting enforcement state from clients with the same or a higher certificate checking mode.
-
Added support for PKG file type to Custom Executable distribution.
-
Support for enforcing virtual channel restrictions with Blast protocol. This list overrides any settings applied through the Horizon Agent.
-
Added support in Web Reverse Proxy for accessing intranet resources using NTLM authentication. In this case, Unified Access Gateway acts as an Identity Bridge to convert SAML into NTLM for back-end resource access.
-
Enhancements in SAML authentication for the Admin UI administrator login.
-
Configuration of static Service Provider entity id that is included in the Service Provider’s metadata.
-
Option to sign SAML AuthNRequest with TLS certificate installed on admin interface.
-
Added support to Tunnel Edge Service for optional Configuration ID parameter (used in future UEM release).
-
Logging improvements and troubleshooting enhancements.
-
Updates to Photon OS package versions and Java component versions.
Release Notes
- Horizon Server
- Horizon Client for Android
- Horizon Client for Chrome
- Horizon Client for iOS
- Horizon Client for Linux
- Horizon Client for Mac
- Horizon Client for Windows
- Horizon HTML Access
- App Volumes
- Dynamic Environment Manager
Documentation
What’s New In Horizon 2306 – Now Generally Available
What’s New In Horizon 2306 – Now Generally Available
Overview
Just released and made generally available on 07/06/2023 is Horizon Version 2306. This is the most current release of Horizon View from VMware. As a reminder this is a majority of the updates below. Look to the links below in the release notes section for full feature information and any additional updates should they happen from VMware.
This particular release has a ton of cool new enhancements around app volumes and our client agent release (CART). In particular for app volumes we have announced App Volumes Manager on Azure AVD with Azure File Shares (Solution Preview)and App Volumes for Amazon AppStream 2.0 Technical PreviewIn future posts I will be going over some these enhancements.
Horizon Server and Instant Clones
- Session load distribution across CPA pods (Session Count approach).
- Block connection to server if client doesn’t validate certificates.
- Allow admins to configure certificate mapping.
- Persistent disk support for Instant Clones.
- Provide fixed timer for discarding SSO credentials without disconnecting Desktops/Apps.
Client and Agent Release
- Horizon Recording support for LinuxVDI.
- Fido2 WebAuthN redirection Windows Client.
- DEEM: Mac client & .pkg installer
- Mac scanner forward vendor-specific options.
App Volumes
- AV Manager on Azure AVD with Azure File Shares (Solution Preview)
- vSphere 8: Package Attachment Resiliency
- Apps On Demand: URI launch
- App Volumes for Amazon AppStream 2.0 Technical Preview
Dynamic Environment Manager
- Support for periodically refreshing DEM configuration.
- Support for collecting telemetry data from DEM Management console
- Support for configuring Horizon. browser content redirection policy.
Unified Access Gateway
-
Added compatibility with Horizon Connection Server’s support for setting enforcement state from clients with the same or a higher certificate checking mode.
-
Added support for PKG file type to Custom Executable distribution.
-
Support for enforcing virtual channel restrictions with Blast protocol. This list overrides any settings applied through the Horizon Agent.
-
Added support in Web Reverse Proxy for accessing intranet resources using NTLM authentication. In this case, Unified Access Gateway acts as an Identity Bridge to convert SAML into NTLM for back-end resource access.
-
Enhancements in SAML authentication for the Admin UI administrator login.
-
Configuration of static Service Provider entity id that is included in the Service Provider’s metadata.
-
Option to sign SAML AuthNRequest with TLS certificate installed on admin interface.
-
Added support to Tunnel Edge Service for optional Configuration ID parameter (used in future UEM release).
-
Logging improvements and troubleshooting enhancements.
-
Updates to Photon OS package versions and Java component versions.
Release Notes
- Horizon Server
- Horizon Client for Android
- Horizon Client for Chrome
- Horizon Client for iOS
- Horizon Client for Linux
- Horizon Client for Mac
- Horizon Client for Windows
- Horizon HTML Access
- App Volumes
- Dynamic Environment Manager
Documentation
New Monitoring Options for VMware Horizon Digital Employee Experience for Horizon (DEEM)
New Monitoring Options for VMware Horizon Digital Employee Experience for Horizon (DEEM)
Overview
It’s true that there is no shortage of monitoring choices out there. However, I am extremely excited about one of the newer options provided by VMware as an additional add-on, which is the Digital Employee Experience for VMware Horizon. The great thing about this option is that it utilizes the telemetry data already available from the Horizon Client and Horizon agent, without requiring any new additional installers. In contrast, some other solutions may require the installation of additional binaries, which can be challenging to ask our consumers/users to install, especially when they are unmanaged.
With our next-generation Horizon Control Plane, we have migrated our monitoring to the Workspace ONE Intelligence platform from our CMS (Cloud Monitoring Service). This opens up a whole new world of opportunities for observability and workflow automation using Workspace One Freestyle Orchestrator, notifications and other workflows can be generated from the captured telemetry events. Some of the integrations include Slack Web API, Workspace ONE UEM, Service Now and your own connectors for enterprise systems (REST API’s).
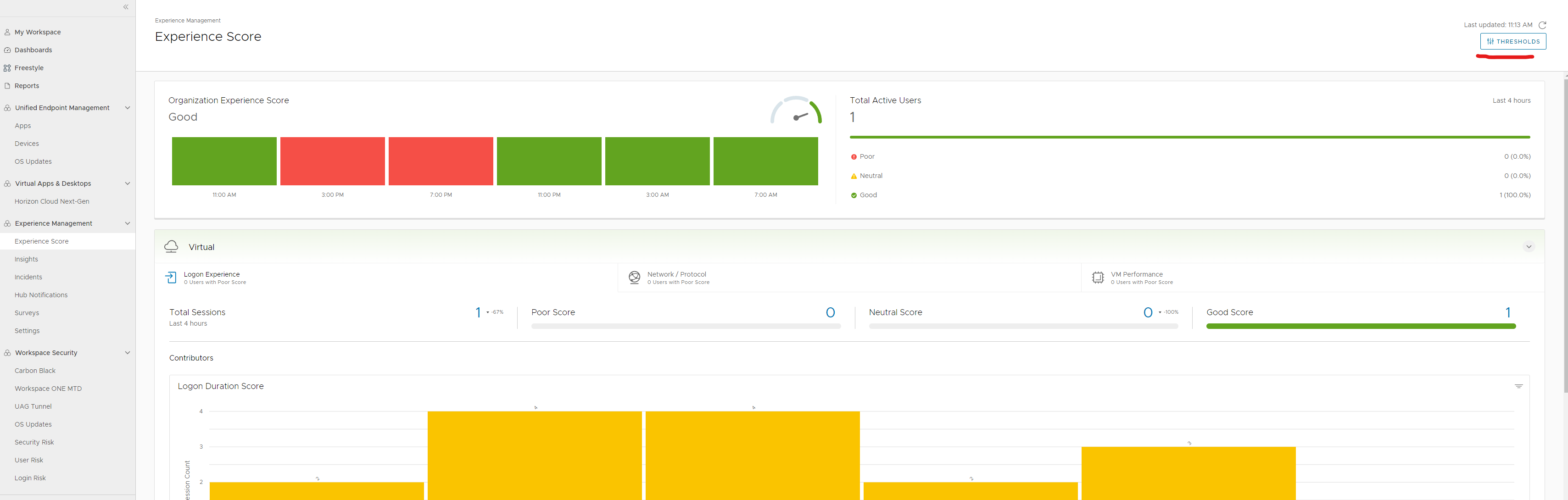
We all strive to create a great experience for our end consumers/users. Our goal is to build secure, performant, and resilient environments. (I’ve often heard from my customers that VDI is the most stable environment.) This monitoring option is an additional step to reinforce the experience we create because certain factors are beyond our control, such as the device they use, the last mile connectivity, and their location. We track VM performance, network performance, and logon times. We utilize this telemetry to generate an overall organization experience score throughout the day. In this post I will go over briefly what dashboards there are and how to set up a notification on an event from Workspace One Freestyle Orchestrator.
Requirements
- Connect your Horizon deployment to Horizon Cloud using the our edge appliance and have Horizon Cloud manage the deployment.
- One of these licences
- Horizon Universal subscription
- Horizon Apps Universal subscription
- Horizon Apps Standard subscription
- An additional purchase of the Workspace ONE Experience Analytics for Horizon add-on SKU. This will provide the DEEM Digital Employee Experience for VMware Horizon dashboards.
- Horizon Next-gen tenants are automatically set up with intelligence when provisioned.
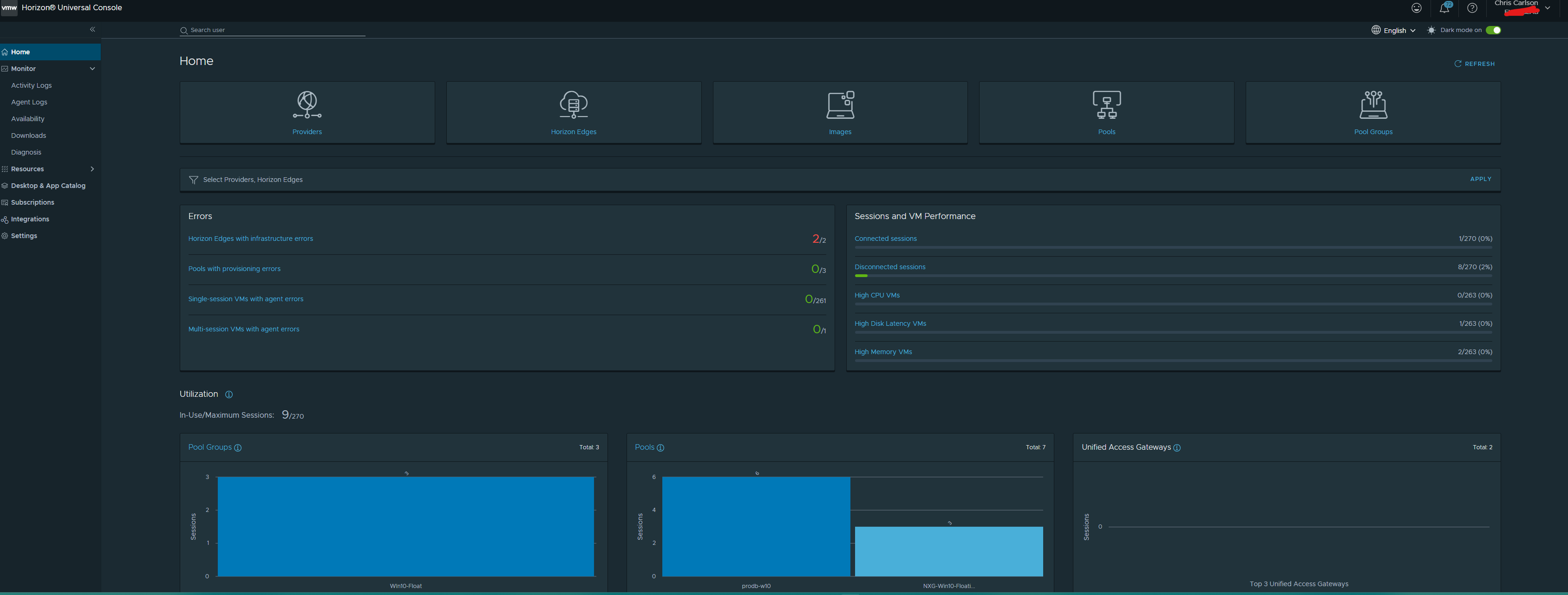
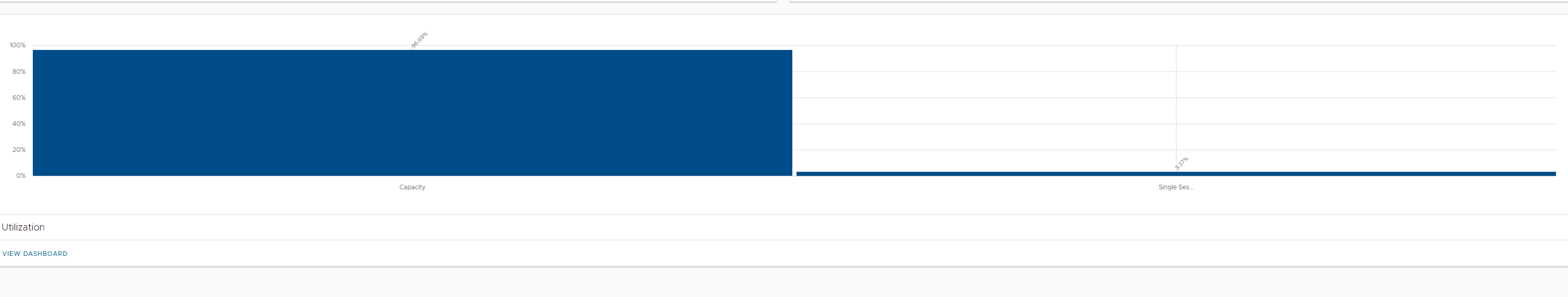
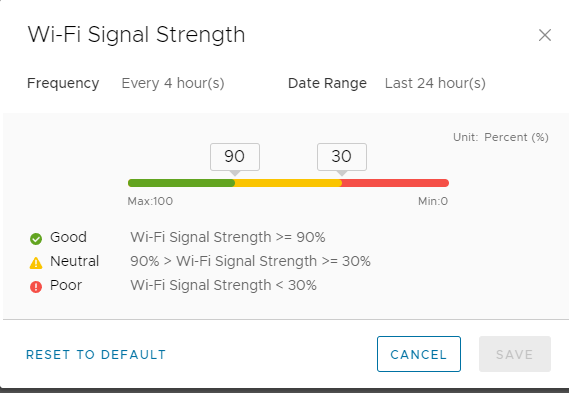
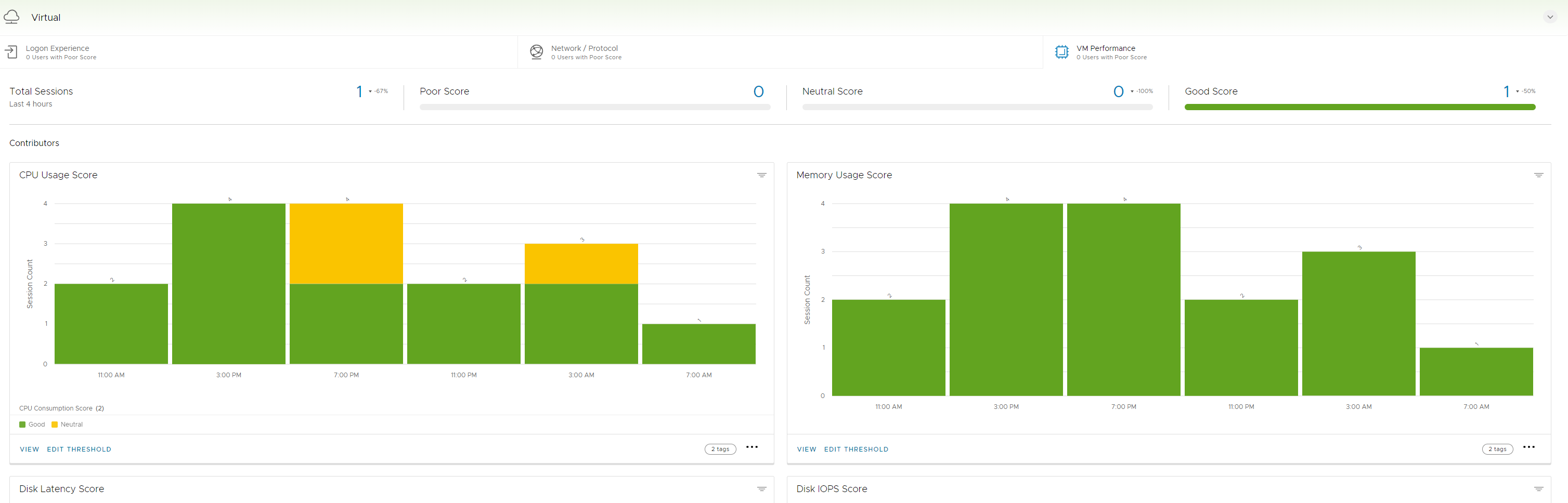
Below I will go over some of the dashboard views. In this first screenshot you can see this is your default display of utilization in your universal console. We can do much more inside of Workspace One.
DEEM – Digital Employee Experience Management
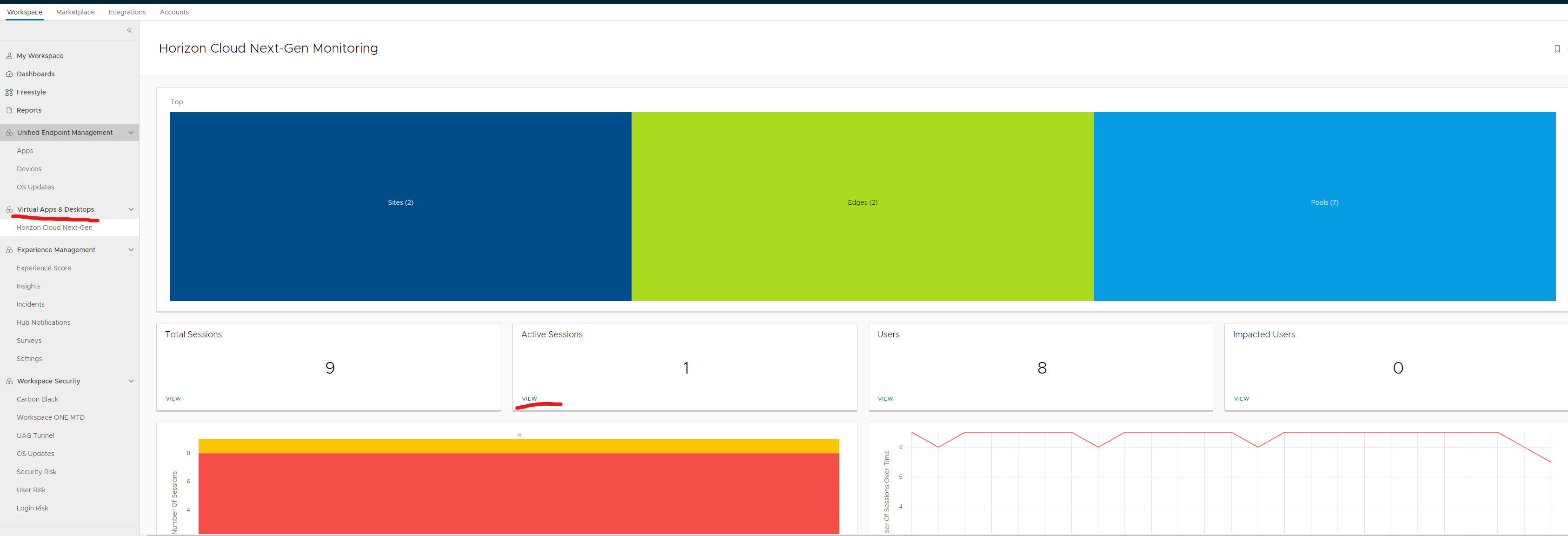
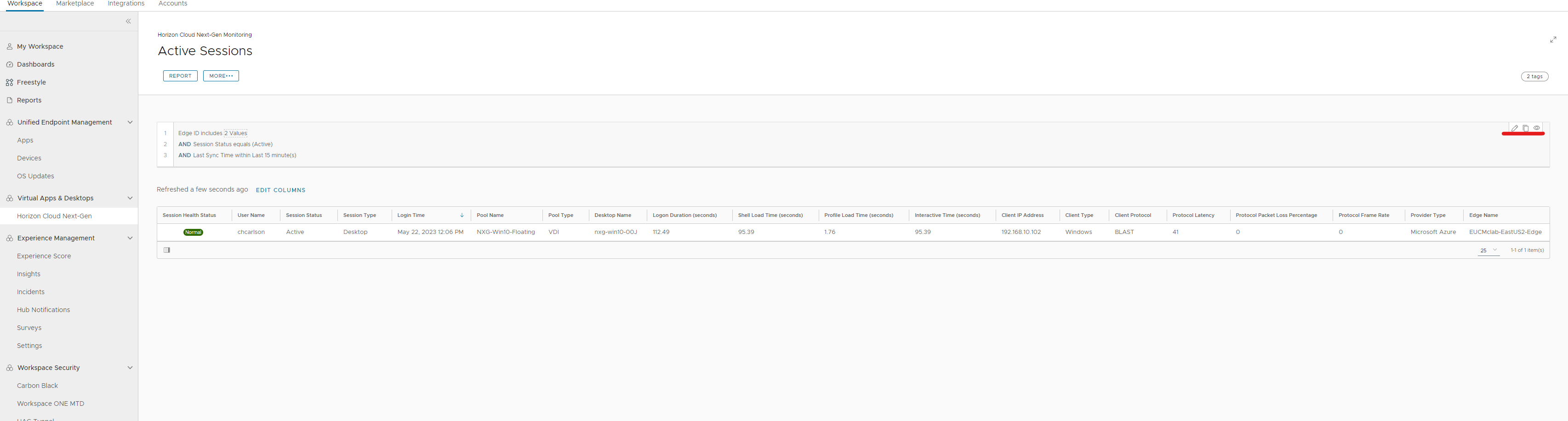
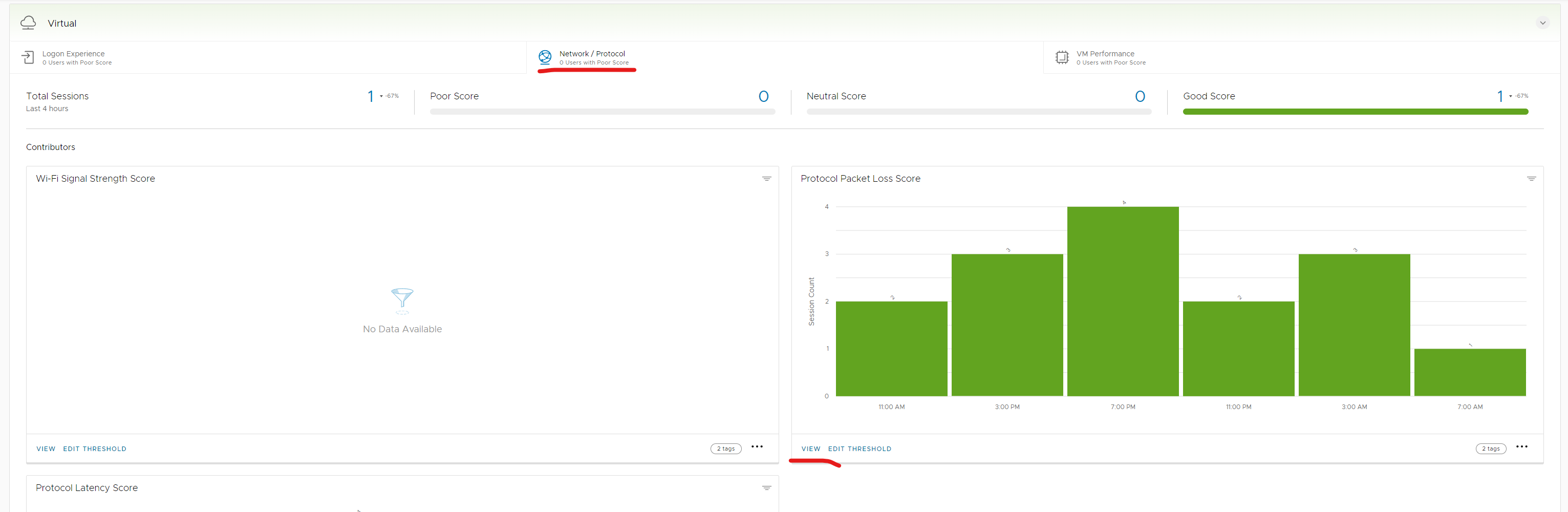
Now available as an additional add on is all of the employee experience metrics and scoring as depicted in the screenshot below.
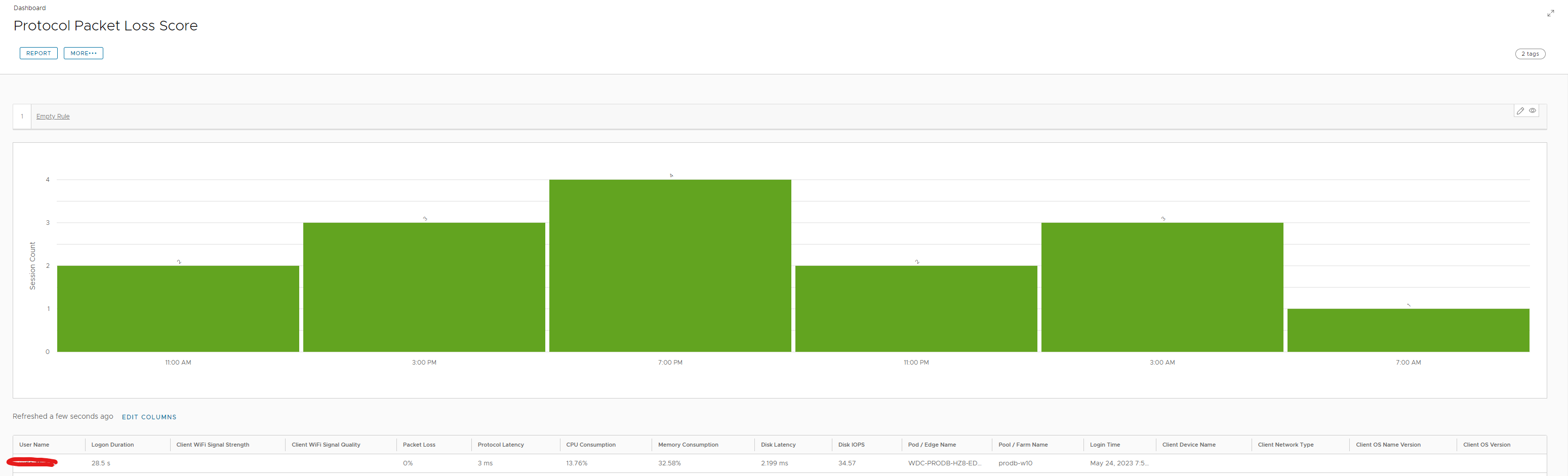
In here you can see more details on your packet loss score. Additionally you can add columns if you want just like shown above to further investigate issues.
Creating Notifications for Horizon with Freestyle Orchestrator
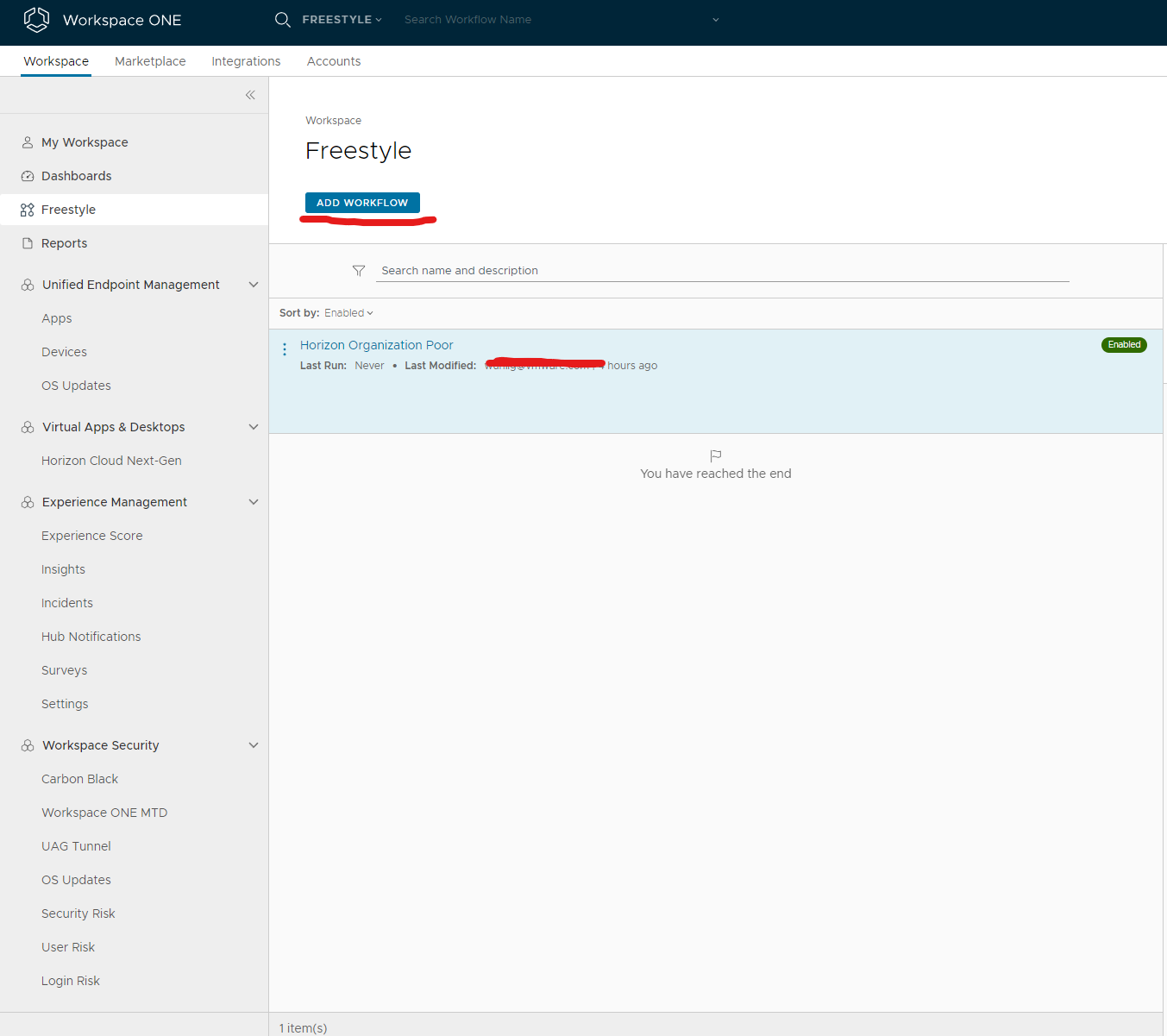
In your workspace one console click Freestyle button and add workflow button to start your first workflow.
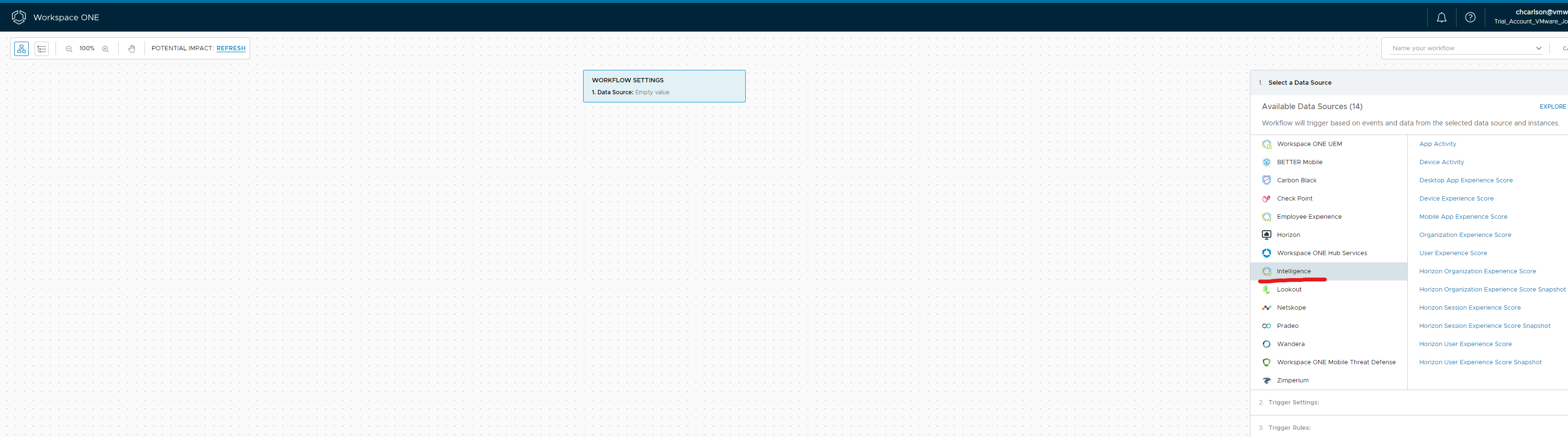
In these two screenshots below you can see the Intelligence data source and the Horizon data source. Intelligence data source has all of the data and telemetry around Digital Employee Experience Management and Horizon has the Horizon components that make up delivery of applications and desktops.
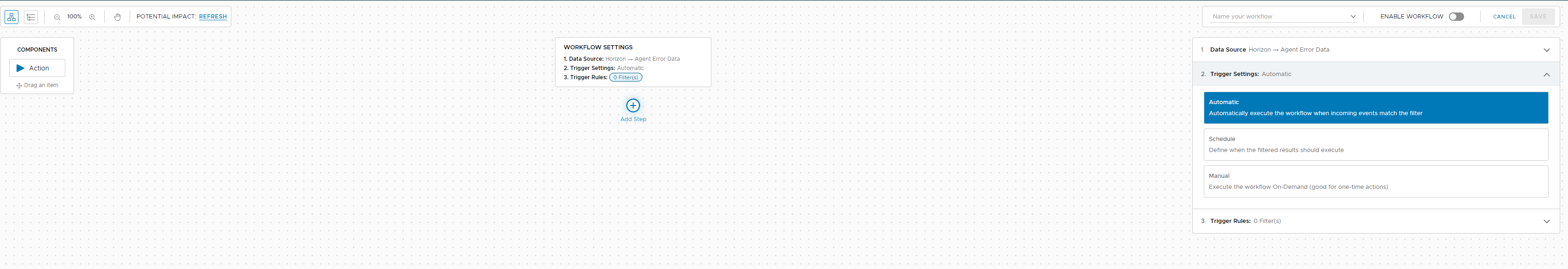
We will go through as an example setting up a workflow to notify an email address of an agent(s) in an errored state. Remember this could be email, slack, service now or your own method. Make sure you select Horizon>Agent Error. Once you have selected that you can chose to execute this workflow manually, schedule it or automatically which is what I am going to do.
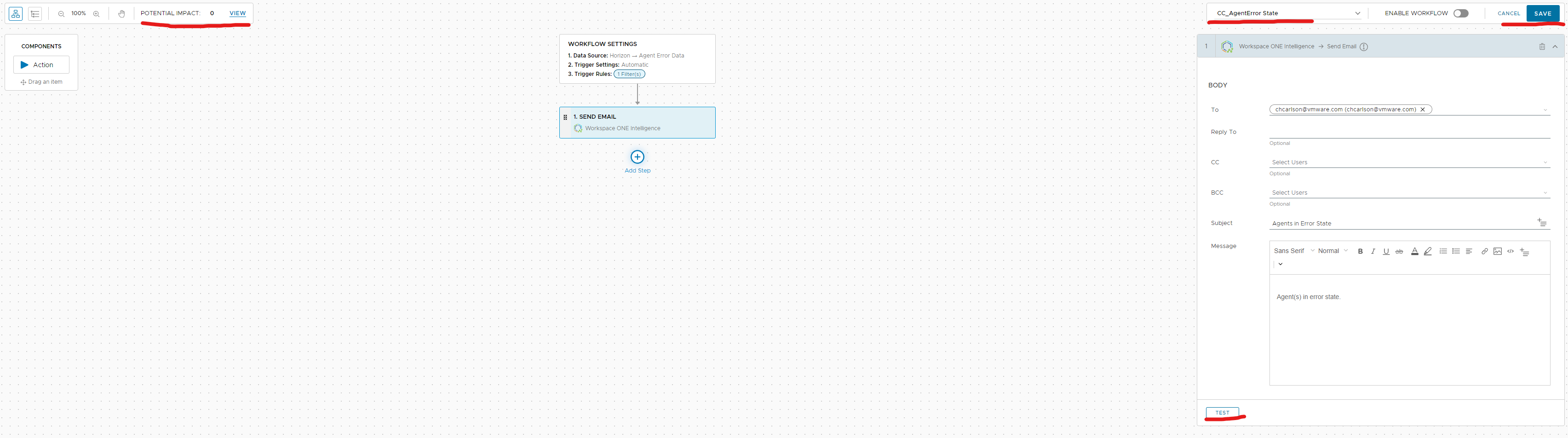
I am going to set my Error Status equals true that way if it is an errored state I will get an email.
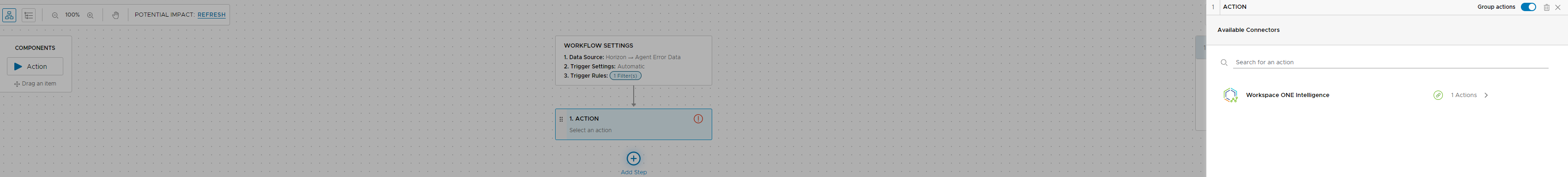
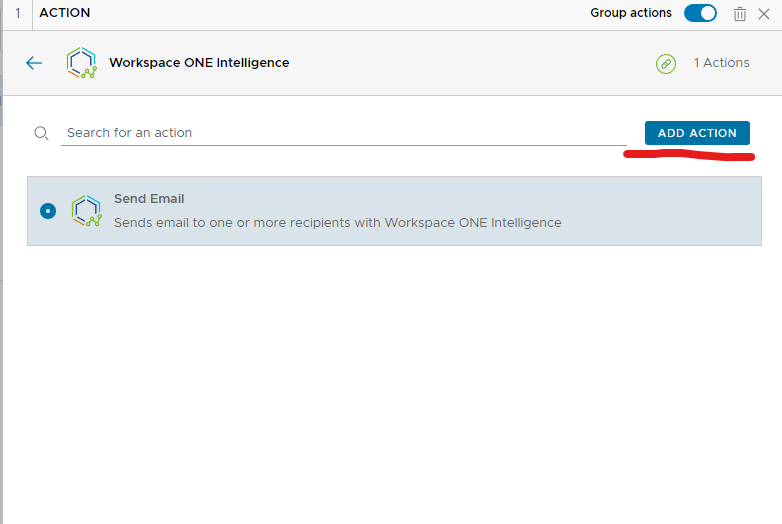
Now we are going to add an additional step to send us the email. I am going to add a step in the workflow and select the send email and click add action.
Now before you enter in your email and test it you can view the potential impact of this workflow before you enable it to so how much it impacts you. If you are satisfied with the results just give a name enable it and click save.
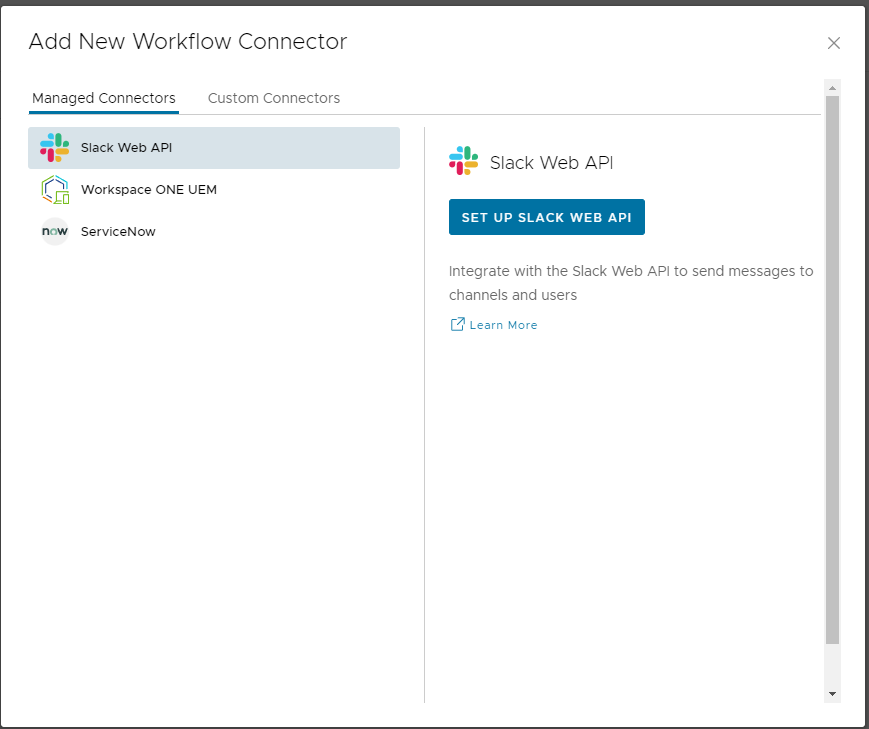
Here is an example of some extra connectors you can add. If you are looking to setup additional workflow connectors in Workspace One go to Integrations tab > Workflow connectors > click the add button.
Microsoft Windows Defender Anti-Virus and App Volumes Scanning Behavior
Microsoft Windows Defender Anti-Virus and App Volumes Scanning Behavior
Overview
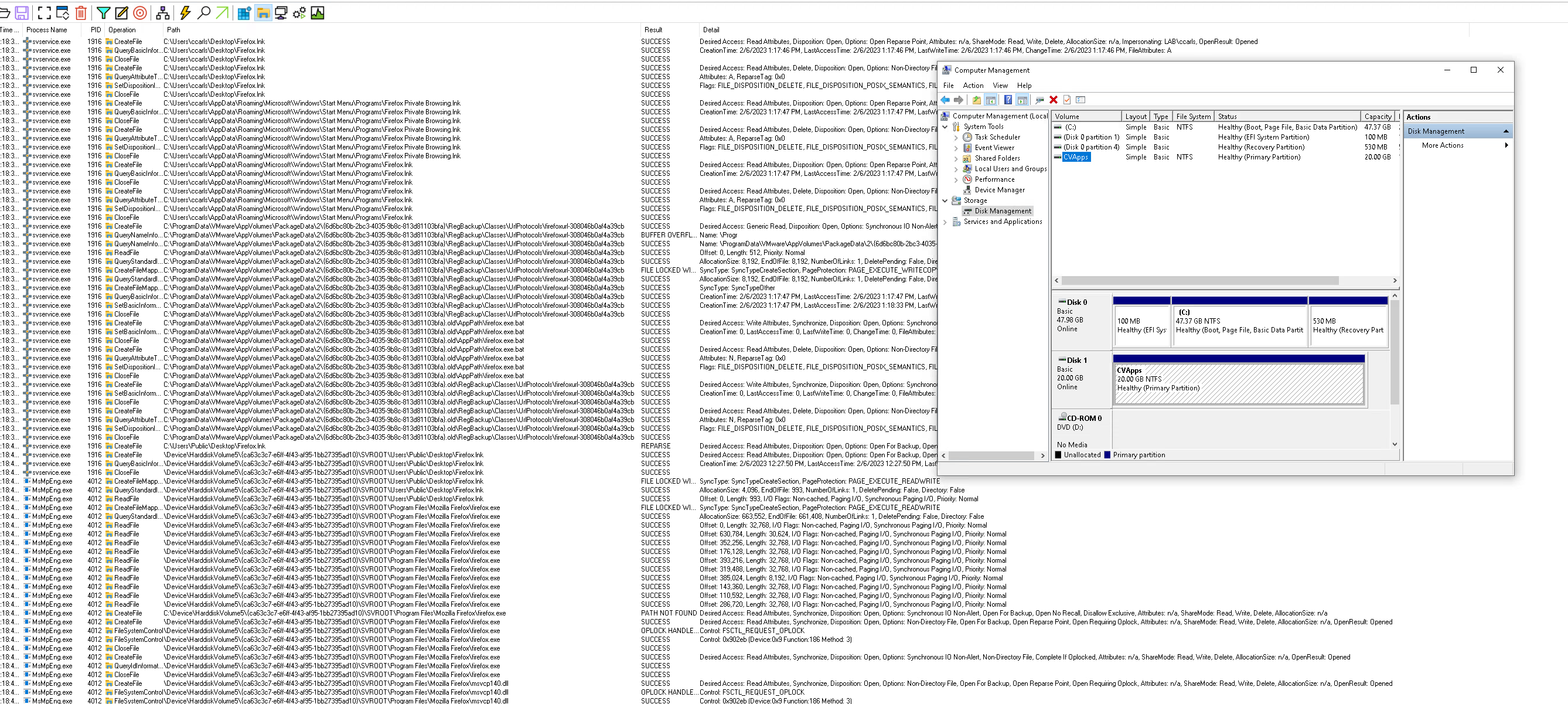
Have you ever been curious about the process that takes place when you initiate an on-demand launch of an App Volumes application on a Windows desktop? Specifically, let’s consider a scenario where we have a Windows 10 Operating System with its default Windows Defender antivirus program. In the screenshot provided, we can observe the behavior of the real-time scanning feature of Windows Defender Antivirus.
To provide some context, the Windows Defender Antivirus program is designed to protect your system from potential threats by continuously monitoring files, programs, and activities on your computer. When you launch an App Volumes application on demand, Windows Defender Antivirus kicks in to scan the application and associated files in real time. Notice that their is a new drive mounted with that application. It is aware of that as well.
In the case of the screenshot I mentioned, the machine where the application was launched was connected to the internet. Windows Defender Antivirus, as part of its functionality, relies on internet connectivity to enhance its scanning capabilities. It utilizes the internet to download the latest virus definition updates, access cloud-based protection services, and analyze potential threats against known patterns and signatures.
Steps
- Provision and entitle an application to be delivered to a user or computer on demand from the App Volumes Manager.
- Start Process Monitor from Microsoft.
- Observe results upon clicking on the shortcut in the Process Monitor software.
You can download the Process Monitor from Microsoft Here
Horizon Feature Parity Comparison on AVS VMCAWS GCVE OCVS
Horizon Feature Parity Comparison on AVS VMCAWS GCVE OCVS
Overview
If you have been thinking about leveraging different cloud providers from any one of VMware’s partners, it is important to note that some capabilities might become available at different times in each of the solutions. Also, I think it is important to remember that what I am talking about here is running vSphere in an IaaS model with one of these landing zones, and not native Azure as that would be our Horizon Cloud service on Azure.
What is interesting and makes things a bit easier for you is when you look at each landing zone’s KB, you can assume that any feature not listed in the table is supported. This makes things easier to consume. I have put the KBs together for you below
Feature Parity KB articles for each solution
Horizon 2212 New Feature App Volumes Apps on Demand Overview and Configuration Part Two
Horizon 2212 New Feature App Volumes Apps on Demand Overview and Configuration Part Two
Overview
This article is a continuation of my first part for published applications on demand for on-premise horizon. If you got brought to this article via search and need to start from the beginning please start here: Horizon 2212 New Feature App Volumes Apps on Demand Overview and Configuration
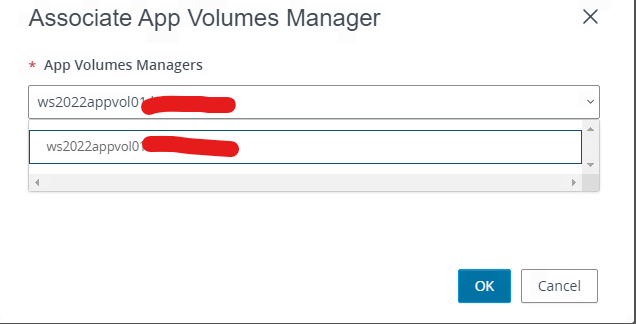
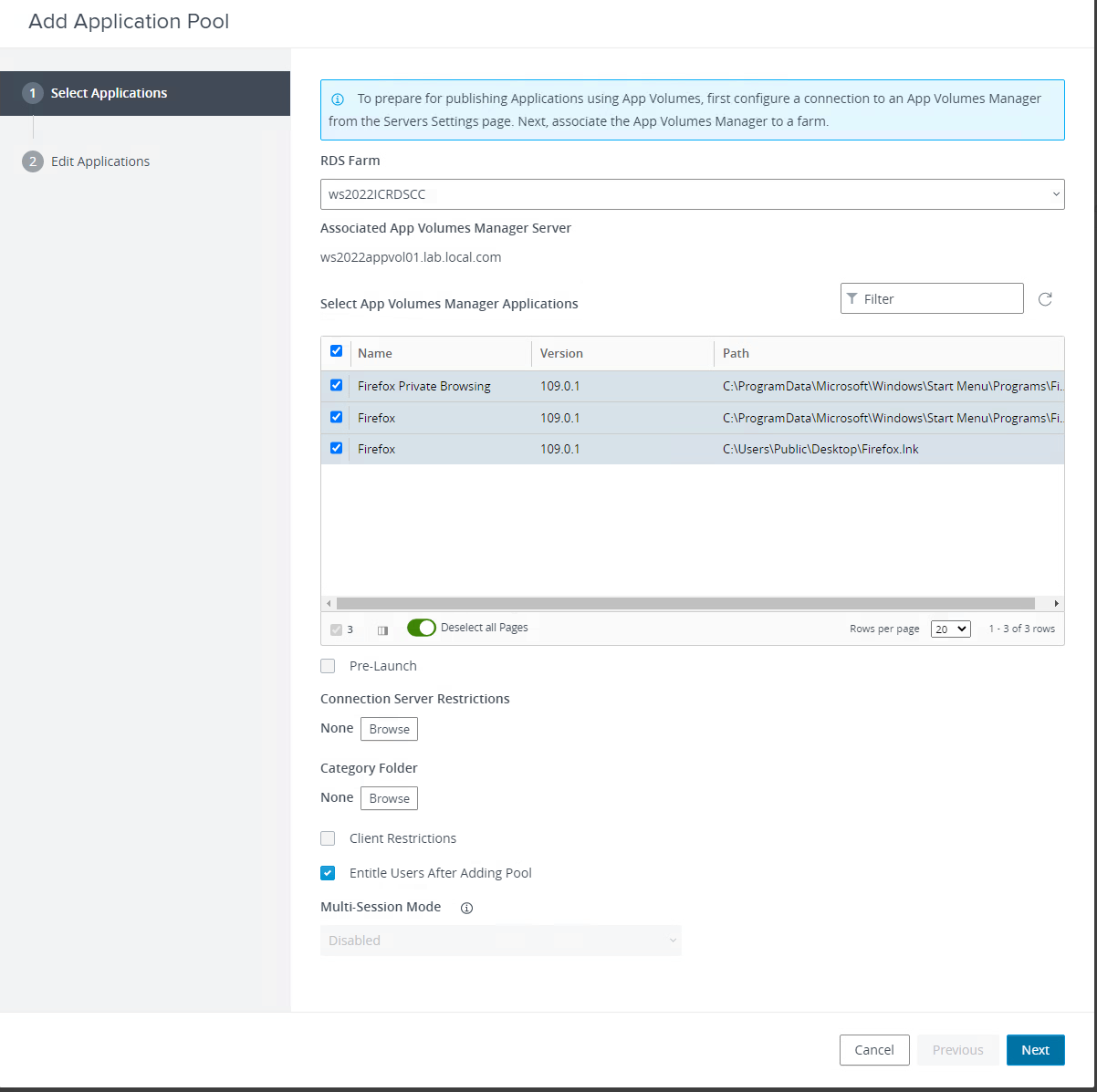
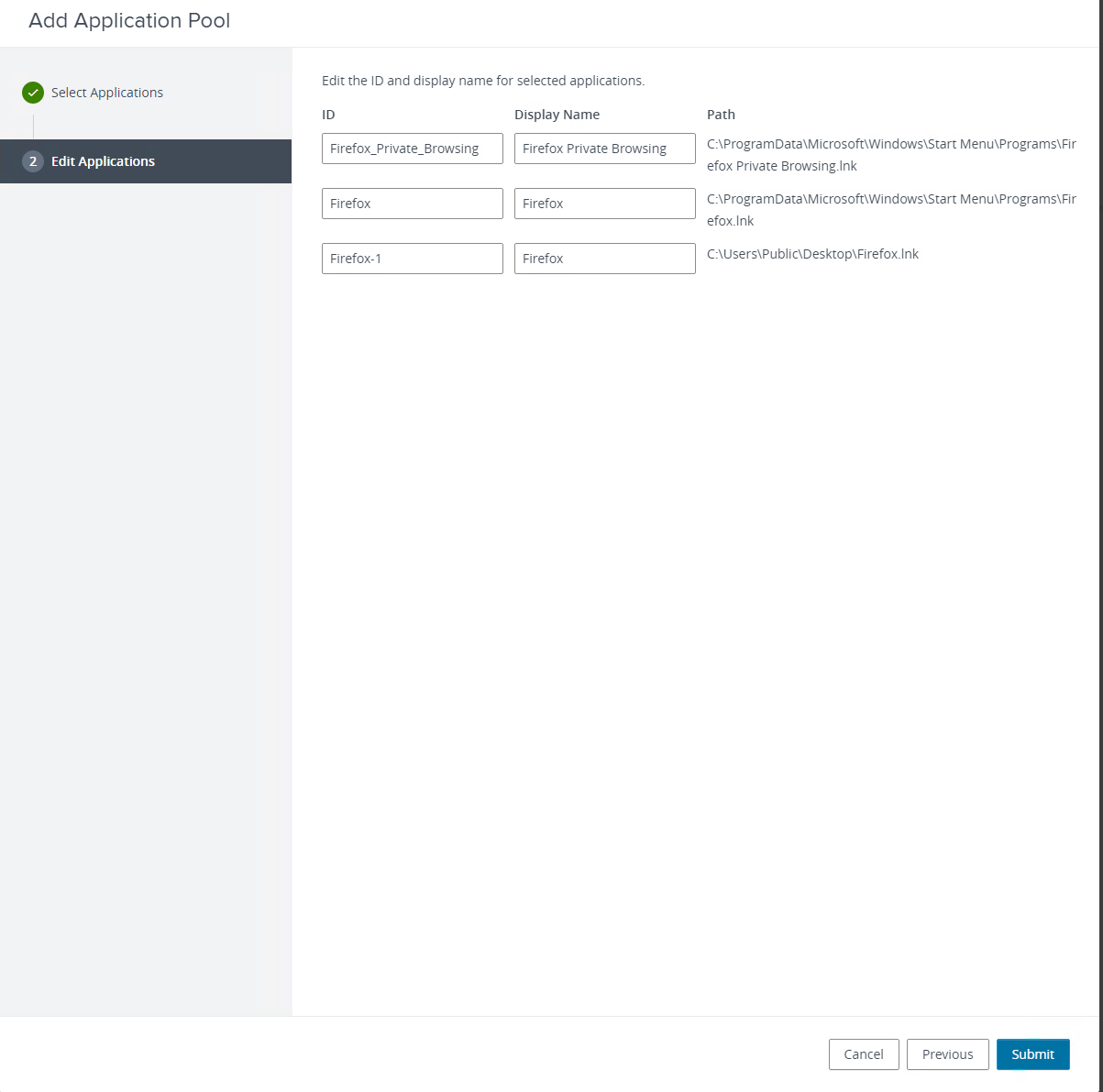
First we will go into the Horizon Connection server>Farms>Farm Next we will associate the farm with an App Volumes Manager with the farm. A farm can be associated with one App Volumes manager but a Manger can be associated with many Farms.
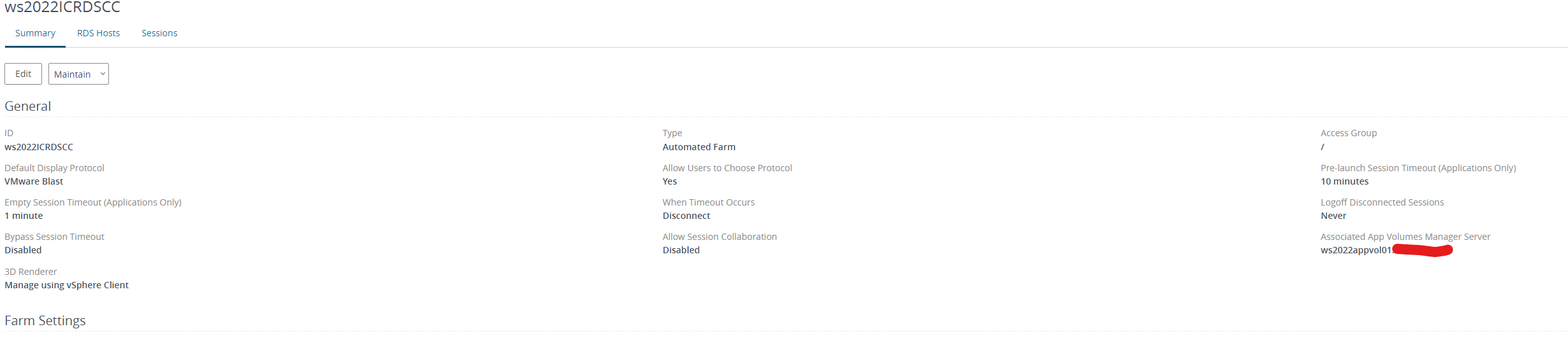
Below you can see the new association in the farm.
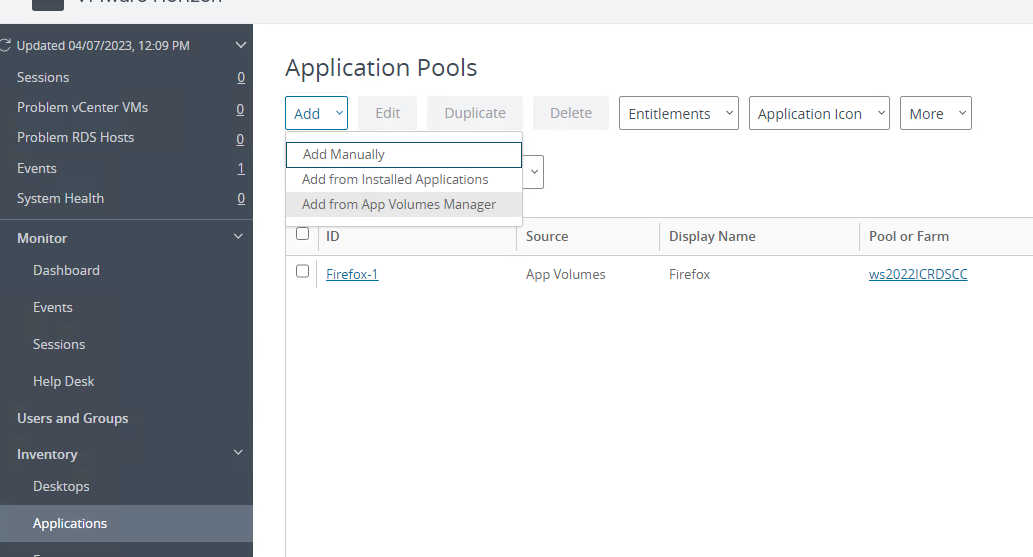
Next in the Horizon Connection server>Applications>Add>Add from App Volumes Manager
After this is complete you will be able to launch your horizon client and consume the new published app delivered on demand!
What’s New In Horizon 2303 – Now Generally Available
What’s New In Horizon 2303 – Now Generally Available
Overview
Just released and made generally available on 03/30/2023 is Horizon Version 2303. This is the most current release of Horizon View from VMware. As a reminder this is a majority of the updates below. Look to the links below in the release notes section for full feature information and any additional updates should they happen from VMware.
Horizon Server and Instant Clones
- Instant Clone Sysprep customization now supports a adding vTPM device for clones.
- Improvement in snapshot management – Snapshot vmdk files of the parent image are now deleted from the datastore when the corresponding snapshots are deleted from the vCenter.
- Instant Clone troubleshooting – Admins can now see timestamp along with pool provisioning errors in the Horizon console.
Client and Agent Release
- Support AV1 Encoding on desktops with Intel ATS-M GPUs
- Windows Client Blast only Bad internet connection warning
- URL redirection rules based on IP address
- BlastCodec support for Mac ARM
- Suppress broker time out message
- Proxy authentication
- Screen shipping for media offload
- Individual Application sharing
- Browser content redirection for Linux client.
- iOS & Android client support for Horizon V2 Next-Gen.
- BlastCodec client performance improvement.
- Improved Blast connection failure diagnostic information.
App Volumes
- Agent Credentials for File Shares
Dynamic Environment Manager
- Support for searching DEM configuration.
- Support for running custom commands as SYSTEM Context.
- Support for FlexEngine command-line option to apply NoAD Settings on-demand.
Release Notes
- Horizon Server
- Horizon Client for Mac
- Horizon Client for Windows
- Horizon Client for Linux
- Horizon Client for iOS
- Horizon Client for Android
- Horizon Client for Chrome
- Horizon HTML Access
- App Volumes
- Dynamic Environment Manager